A wearable glove-like device that can “hack” and influence dreams, Team of MIT researchers is developing this device called “Dormio”. It senses the users slipping into hypnagogia which is the semi-lucid state between wakefulness and sleep. It plays prerecorded audio, typically comprising one word. The researchers have found that the audio content successfully showed up in people’s dreams. They have experimented with 50 people. The possibilities are endless to help cure traumatic memories or bad nightmares. However, if they move closer to commercialization there could be serious ethical concerns as…
Read MoreMonth: April 2020
Zoom Zero-Day Exploits Sold for $500,000
Zoom popular video conferencing app has been in a huge controversy recently for sending data to Facebook along with encryption issues which allowed hackers to upload the Zoom recordings on Youtube. It has been rumored that the zoom account is being sold by hackers on the dark web There are two Zoom zero-day exploits one for Windows and one for Mac OS which is priced for $500,000. The major flaws in the app allow hackers to attack the user accounts and spy on their calls. Windows Zero-Day in…
Read MoreRead Write File using File Stream in Dot Net
Read file in byte array in vb.net : Public Function Reader(ByVal FilePath_ As String) As Byte() Dim BytArr(FileSystem.FileLen(FilePath_) – 1) As Byte Using fs As New FileStream(FilePath_, FileMode.Open, FileAccess.Read, FileShare.ReadWrite) fs.Read(BytArr, 0, BytArr.Length) fs.Close() End Using Return BytArr End Function Read file in String : Public Function ReaderString(ByVal FilePath_ As String) As String Dim data_str As String Using fs As New FileStream(FilePath_, FileMode.OpenOrCreate, FileAccess.ReadWrite, FileShare.ReadWrite) Using Sr As New StreamReader(fs) data_str = Sr.ReadToEnd Sr.Close() fs.Close() End Using Return data_str End Using End Function Read File with Encoding (using default encoding…
Read MoreInterview questions for SQL server jobs
For all the software developers interested in working on SQL server, we bring you a set of interview questions asked by one of the top IT giants – Tech Mahindra. These questions have been posted by techies – who are presently working with Tech Mahindra, or have previously worked with the IT giant.
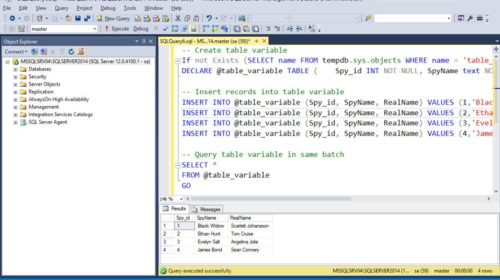
Read MoreSql Server How do Temporary Tables Work?
All of the temporary tables are stored in the tempdb database and can be listed using the query below.
Read MoreEmail provider got hacked, data of millions of users now sold on the dark web
Italian email provider Email.it confirms security breach.
The data of more than 600,000 Email.it users is currently being sold on the dark web.,
“Unfortunately, we must confirm that we have suffered a hacker attack,” the Italian email service provider said in a statement to ZDNet on Monday.
Read More